

The incident happened around 4:30 PM on Friday, "The Last day of the week" at the Accounts/Marketing department of "Finance XYZ" company. There weren't many people in the department, and the remaining were not paying much attention to their surroundings as they were getting ready to head home. After the weekend on Monday while reviewing the security cam footage member of an IT team saw "Eddie" a new intern in the Accounts/Marketing department, plugging a USB into an unauthorized computer (containing sensitive financial and marketing documents), interacting with computer and unplugging the USB before heading out. As the incident happened 2 days ago, and not having enough knowledge of what Eddie did the security team use caution while asking around and gathering intel to avoid causing suspicion. The only information they were able to find out was that Eddie had a "Toshiba" USB. You are provided with a partial image of the “unauthorized computer" as well as a list of important documents, to investigate what he did and if he stole something sensitive or not?
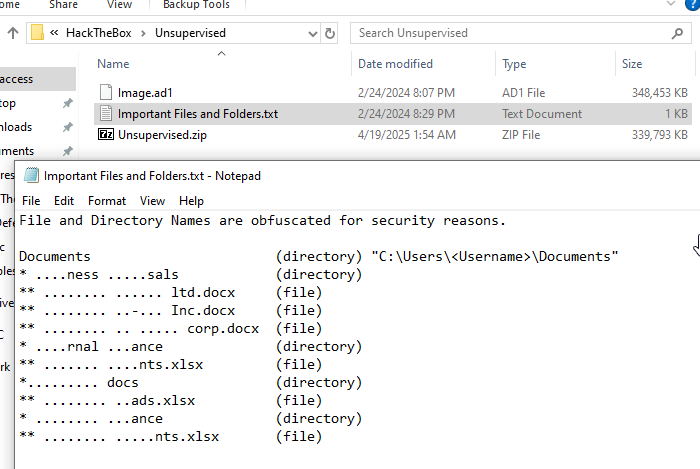
We have 2 files extracted from the sherlock zip file, first is disk image file with ad1 extension and the second is a text file that contains informatiom about important files and folders but it was obfuscated
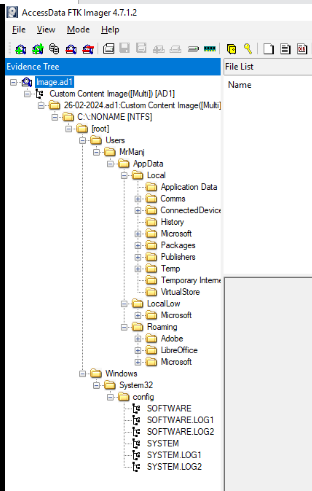
Since the image file is ad1 so we have to use FTK imager to analyze this image file and we can see that there is only a single user folder on this machine and we also have SYSTEM and SOFTWARE hive as well.
Task 1: Find out the time zone of victim PC. (UTC+xx:xx)
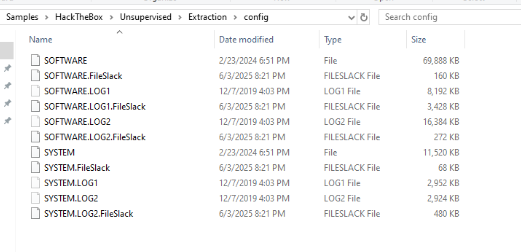
First we can mount disk image or extract config folder with both registry hives to our machine.
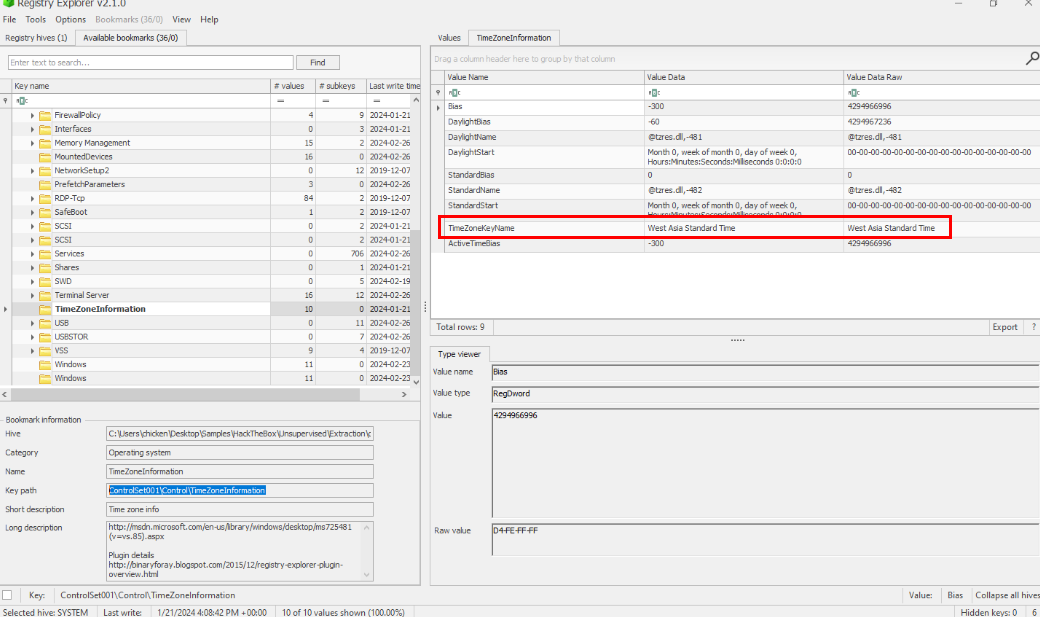
Now lets open SYSTEM hive with Registry Explorer and check out ControlSet001\Control\TimeZoneInformation key that was already bookmarked by default then we can see that the timezone of this PC is West Asia Standard Time.
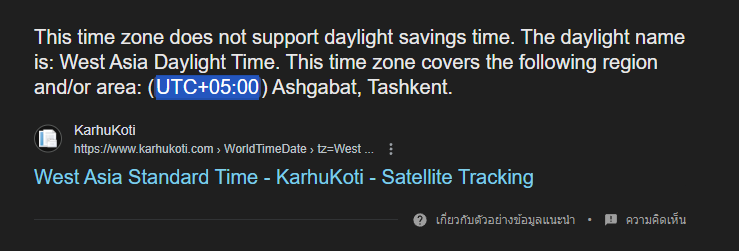
With a quick google search reveal the UTC time format and we can use this to answer this question right away.
UTC+05:00
Task 2: Employees should be trained not to leave their accounts unlocked. What is the username of the logged in user?
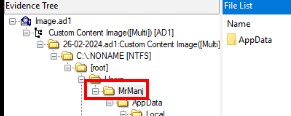
Normally I would look up SAM hive but there is none on this sherlock so the only user available to us on is MrManj, the author of this sherlock 😂
MrManj
Task 3: How many USB storage devices were attached to this host in total?
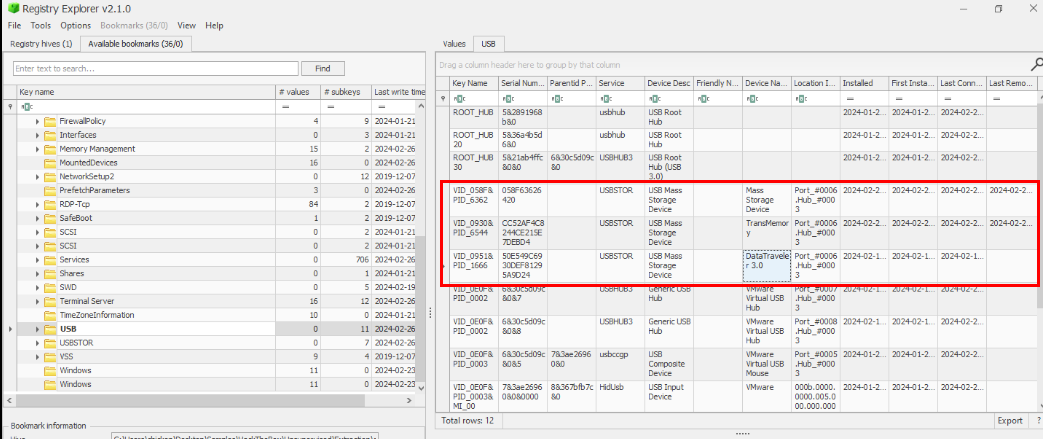
Going back to registry explorer, we can now look at USB key which we will see that on the "Device Description" field, we can filter with something like "USB Mass" or "Mass Storage" to get all USB storages devices attached to this host, or we can just filter for "USBSTOR" on the service field as well.
Now we have total of 4 devices but then for some reason, the correct answer of this question is 3 so maybe "Mass Storage Device" could be the disk storage of C drive.
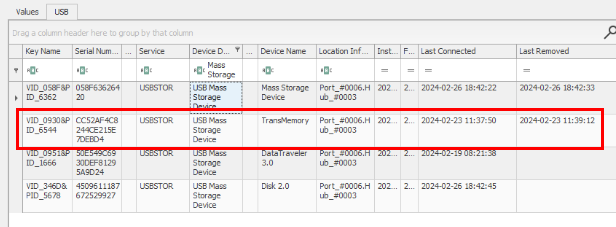
Then from the scenario, we also know that Eddie using "Toshiba" USB so Toshiba TransMemory might be the one that plugged into the machine and did something dirty so we will get last connected and last disconnected time to answer task 4 and 5 before proceeded to find out what happened during this time.
3
Task 4: What is the attach timestamp for the USB in UTC?
2024-02-23 11:37:50
Task 5: What is the detach timestamp for the USB in UTC?
2024-02-23 11:39:12
Task 6: Which folder did he copy to the USB?
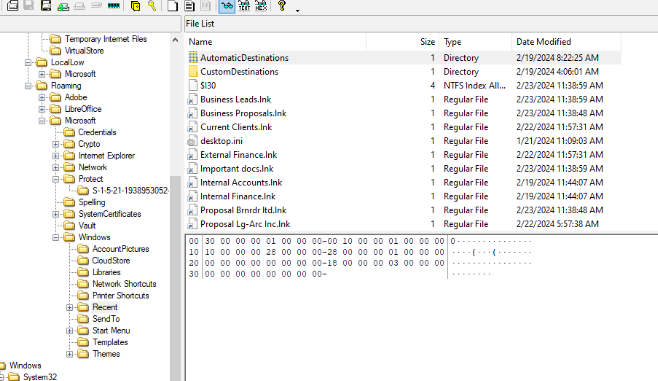
Normally, I would check for ShellBags for UEBA but there is no NTUser.dat hive from this disk image file so the only option here is Jumplists right here.
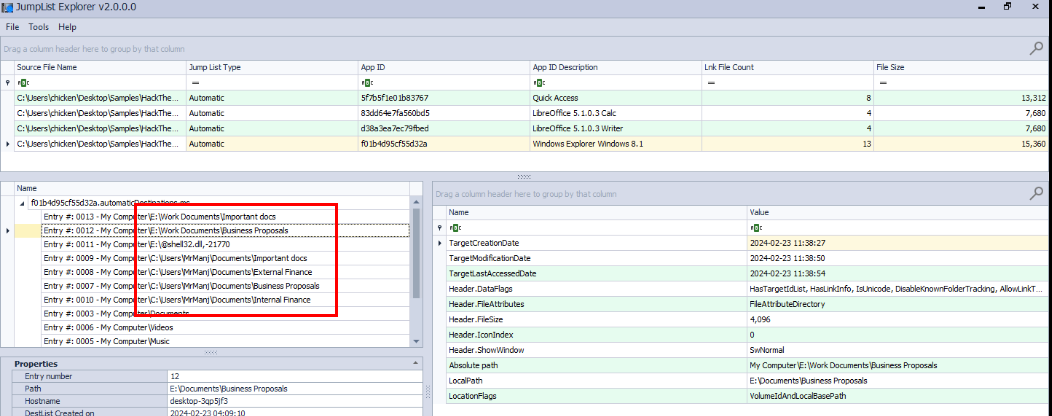
After exported it and use JumpLists Explorer to open it, we can see that there are 3 applications that JumpLists collected which are Windows Explorer, Libre Calc and Libre Writer.
Libre Calc is for xls file and Libre Writer is for docx file. which leaves us to Windows Explorer which is expected and as we can see that there are a folder with 2 sub-folders were opened from E drive and this drive is the USB storage drive of Eddie! and we can also see that 2 sub-folders of Work Documents are the copied of "Documents" folder of the author of this sherlock.
Documents
Task 7: There were subfolders in the folder that was copied. What is the name of the first subfolder? (Alphabetically)
Business Proposals
Task 8: Eddie opens some files after copying them to the USB. What is the name of the file with the .xlsx extension Eddie opens?
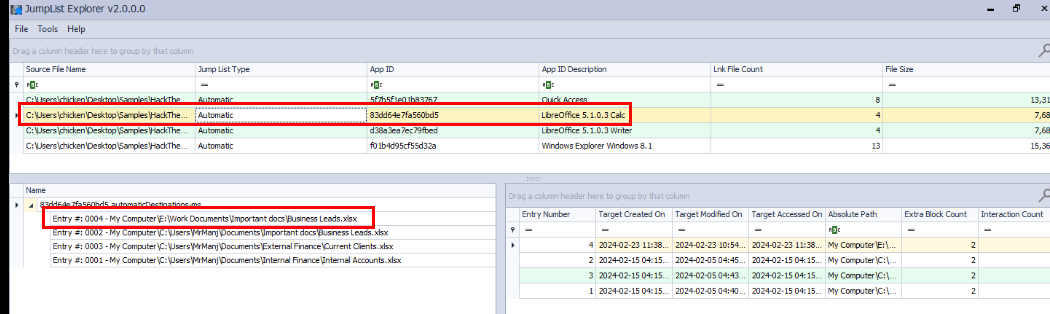
For xlsx file, we have to take a look at files that were opened by Libre Calc and we can see that there is a single file xlsx opened from eddie flash drive.
Business Leads.xlsx
Task 9: Eddie opens some files after copying them to the USB. What is the name of the file with the .docx extension Eddie opens?
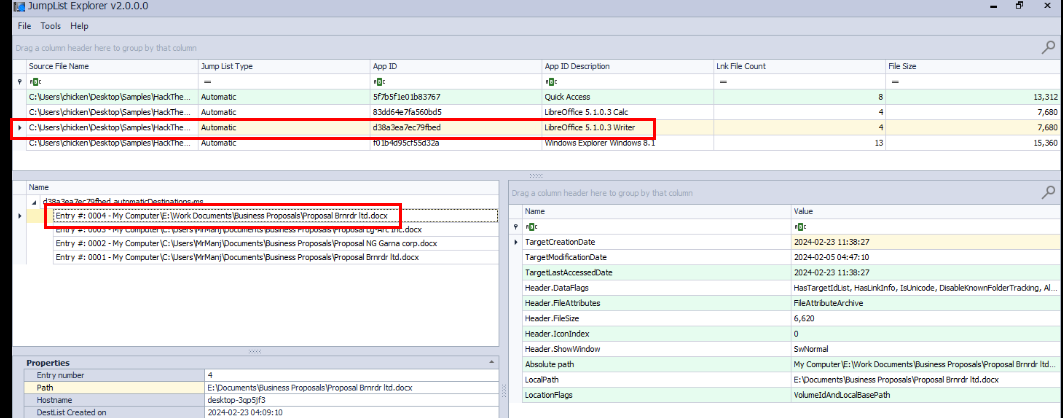
The same goes for docx file that was opened with Libre Writer right here.
Proposal Brnrdr ltd.docx
Task 10: What was the volume name of the USB?
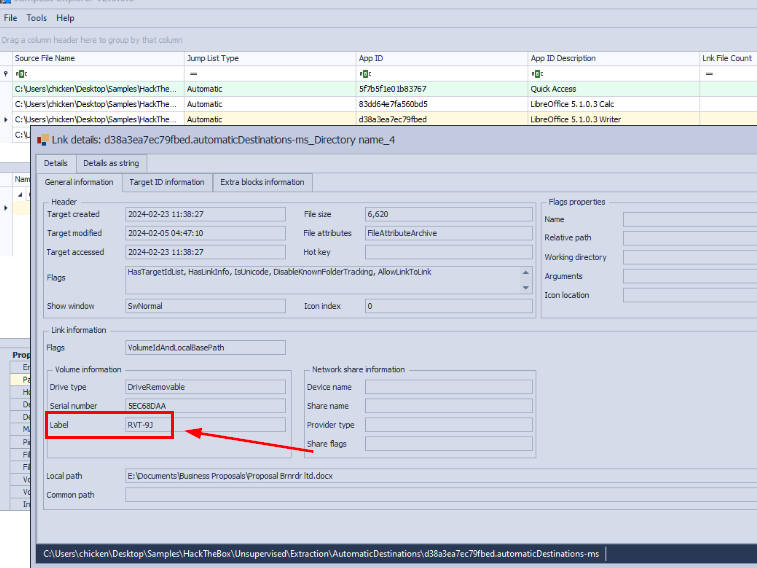
Some might not know that when opened a file on USB storage, JumpLists also stores the volume name/label and serial number of that USB storage as well so what we need to do is to open the detailed of this file and we will see the answer of this question right here.
RVT-9J
Task 11: What was the drive letter of the USB?
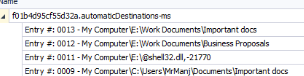
E drive is only a single drive letter other than C and this is correct answer of this question as well.
E
Task 12: I hope we can find some more evidence to tie this all together. What is Eddie's last name?
There is no trace of Eddie on this machine beside his USB storage so how we could find out about this? well author of this sherlock already provides hint for us that "Sometimes, the smallest details in an image can reveal the biggest secrets." so the only source of image on disk image is "Thumbcache" which located at C:\Users\[Username]\AppData\Local\Microsoft\Windows\Explorer
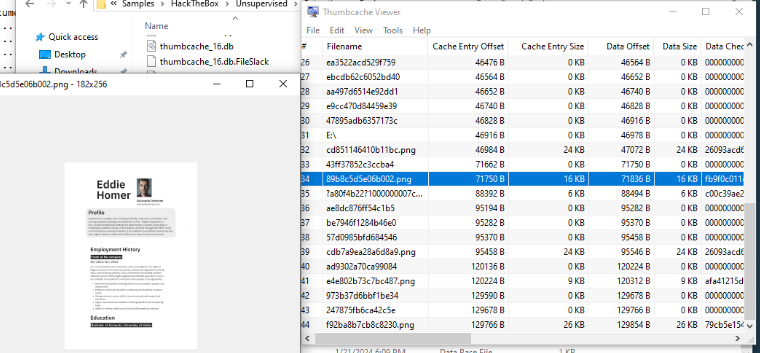
So after exported it out, I used Thumbcache viewer to open thumbcache_256.db file which reveal that author of this sherlock once opened an image of Eddie's resume/CV and its cached here.
Homer
Task 13: There was an unbranded USB in the USB list, can you identify it's manufacturer’s name?
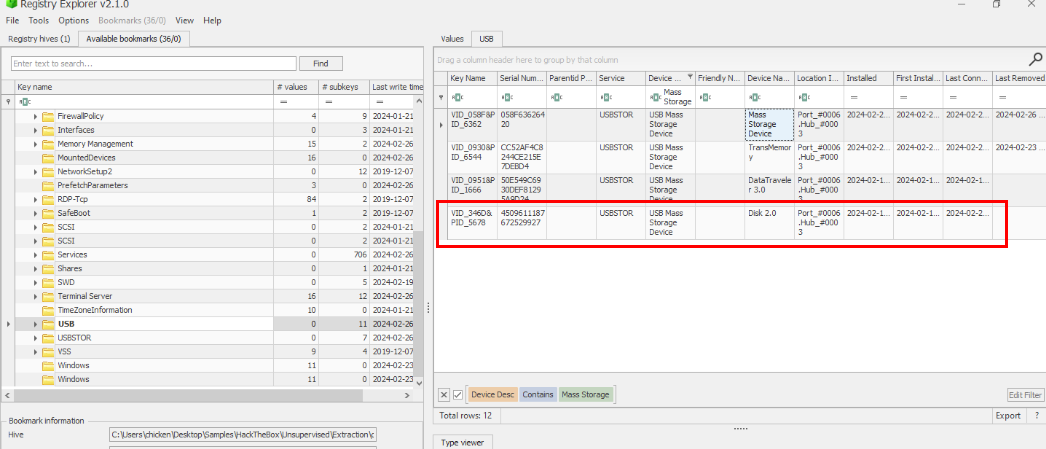
From USB key, we know that DataTraveler belongs to Kingston and TransMemory belongs to Toshiba which leaves us with last one to figured out.
First we will have to dissect Vender ID and Product ID from key name of this device first.
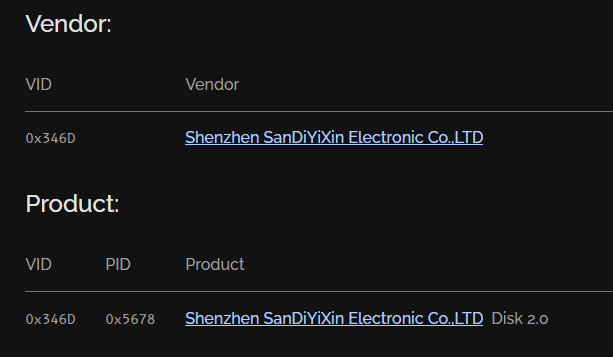
Now we have VenderID = 0x346D and ProductID = 0x5678 so we can use the following website to look up for this device and it reveals the manufacturer name of this product right here.
Shenzhen SanDiYiXin Electronic Co.,LTD
 https://labs.hackthebox.com/achievement/sherlock/1438364/874
https://labs.hackthebox.com/achievement/sherlock/1438364/874